Cyber Security & Resiliency
generate new business value.
Itway has had Cyber Security in its DNA since 1996.
Today, in an increasingly complex world, we support organizations in business growth, and with our Cyber Security & Resiliency offering, we defend against cyber-physical threats to ensure the safe and resilient operation of mission-critical systems and to drive the digital transformation of business.
Cyber secure and resilient organizations enjoy:
- Reduced impact of crises on business performance
- Greater speed of business recovery during crises
- Structural enhancements and innovation in business processes, organization, and digital technologies
- Increased efficiency and protection of the long-term digital growth of the business.
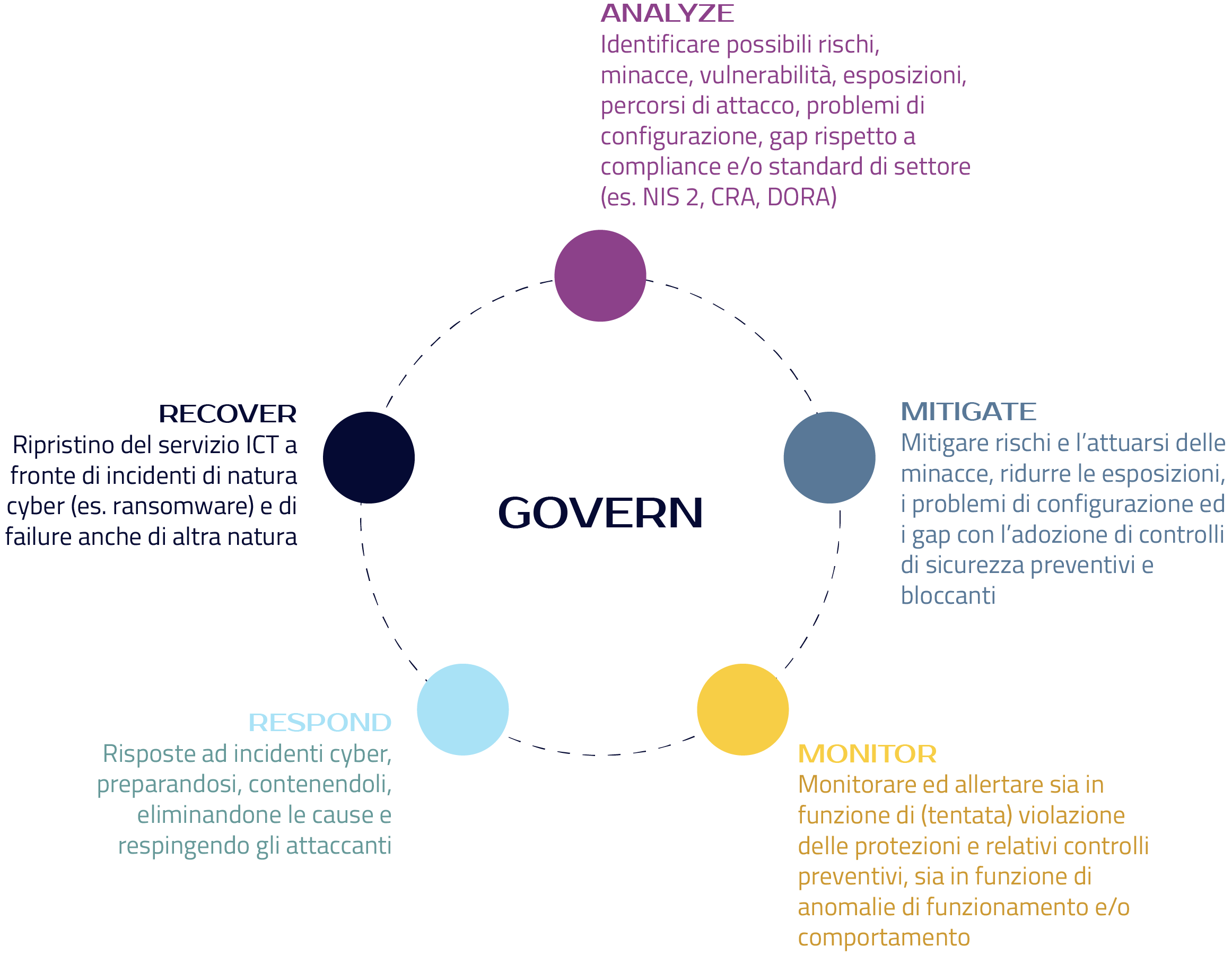
ANALYZE
Identify potential risks, threats, vulnerabilities, exposures, attack paths, configuration issues, gaps in compliance, and/or industry standards (e.g., NIS2, CRA, DORA).
RECOVER
Restoration of ICT services following cyber incidents (e.g., ransomware) and failures of other kinds.
RESPOND
Respond to cyber incidents by preparing, containing them, eliminating their causes, and repelling attackers.
MONITOR
Monitor and alert both in terms of (attempted) breaches of protections and related preventive controls, as well as in terms of operational and/or behavioral anomalies.
MITIGATE
Mitigate risks and the occurrence of threats, reduce exposures, configuration issues, and gaps through the adoption of preventive and blocking security controls.
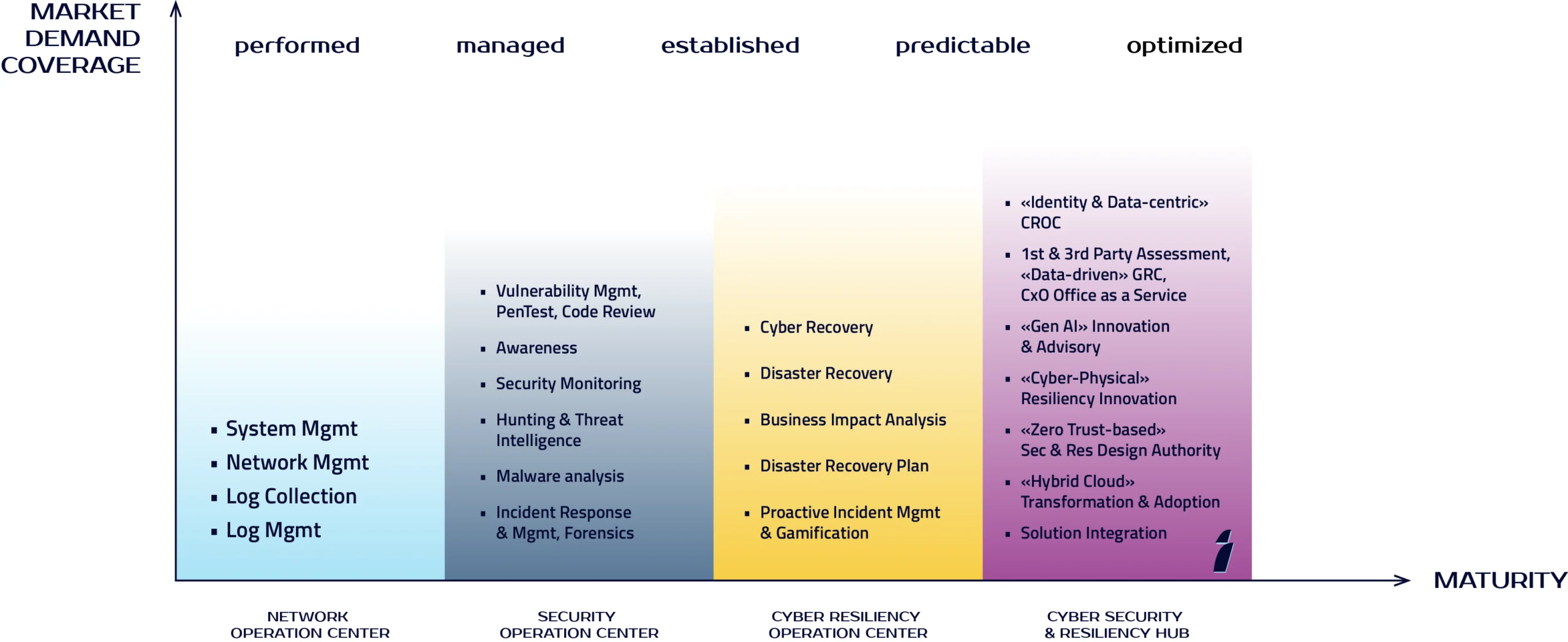
Cyber Power Itway
We have been evolving and innovating since 1996 to provide next-generation Cyber Security & Resiliency services and solutions that support our clients' businesses, and we do this in the following ways:
Preventive
Identifies and protects
Corrective
Detects and responds
Reactive
Recovers from security incidents, disasters, and errors
Adaptive
Transforms and modernizes to increase flexibility and scalability
- Governance, Risk & Compliancewith consulting and solutions for Decision-Making Support, What-if Analysis, and Budget Simulation for NIS 2, IEC 62443, ISO 27001, ISO 22301, NIST CSF, DORA, AI Act, Cyber Resiliency Act, and Machinery Regulation.
- Data-driven GRC and Situational Awareness with Visibility, Understandability, and Control of data from Intelligence Insight on internal and external Attack Surfaces (including Supply Chain with Third Parties and OEMs).
- Observability for Security & Resiliency with a balanced mix of Lock-in Free and Platformization of Metrics, System, Network, Security, and Application Telemetries.
- Assumed Breach Security Strategy, focusing the Security Roadmap on Identity (human and non-human), Least Privilege, Security Hygiene, and Data Protection.
- Software-defined e Generative AI-powered Remediation, to mitigate the impact of High TCO, Skill Shortage, and Technical Debt on the execution of Risk Management Programs.
- Site Reliability Engineering through expertise in Business Process Analysis, Software-defined Automation, and Orchestration.
- Assumed Breach & Assumed Failure Engineering & Operation, combining skills in Crisis Simulation, Crisis Management, Automation, and an Ethical Hacker Mindset.
- DevSecOps con Pipeline Cloud-Native o Open-Source e On-premise
- Generative AI & ML Adoption with expertise ranging from Risk Analysis (AI Act) to ML Ops.
- Cloud Freedom or Platformization depending on use cases and business scenarios, with a mix of both Private and Public Cloud solutions, as well as Commercial and Open-Source options.
- Software-defined and Generative AI-powered Remediation, to mitigate the impact of High TCO, Skill Shortage, and Technical Debt on the execution of Risk Management Programs.
- Governance, Risk & Compliance with consulting and solutions for Decision-Making Support, What-if Analysis, and Budget Simulation for NIS 2 and IEC 62443.
- Security & Resiliency Twin with simulation of Cyber Attack scenarios and Vulnerability Prioritization or Process Failure.
- Secure & Resilient Edge with solutions for Visibility, Next-Gen Segmentation, and Least Privilege suitable for OT and Hybrid contexts.
- Business Process Resiliency with Predictive Maintenance enabled by Machine Learning on Edge Computing and Cloud.
- OT / Edge System Recovery with solutions for Air Gapped infrastructures or those with limited Computing and Connectivity capabilities.
Request information
Would you like to receive newsletters on Cyber? Please complete the form.